API Authentication: A Complete Guide
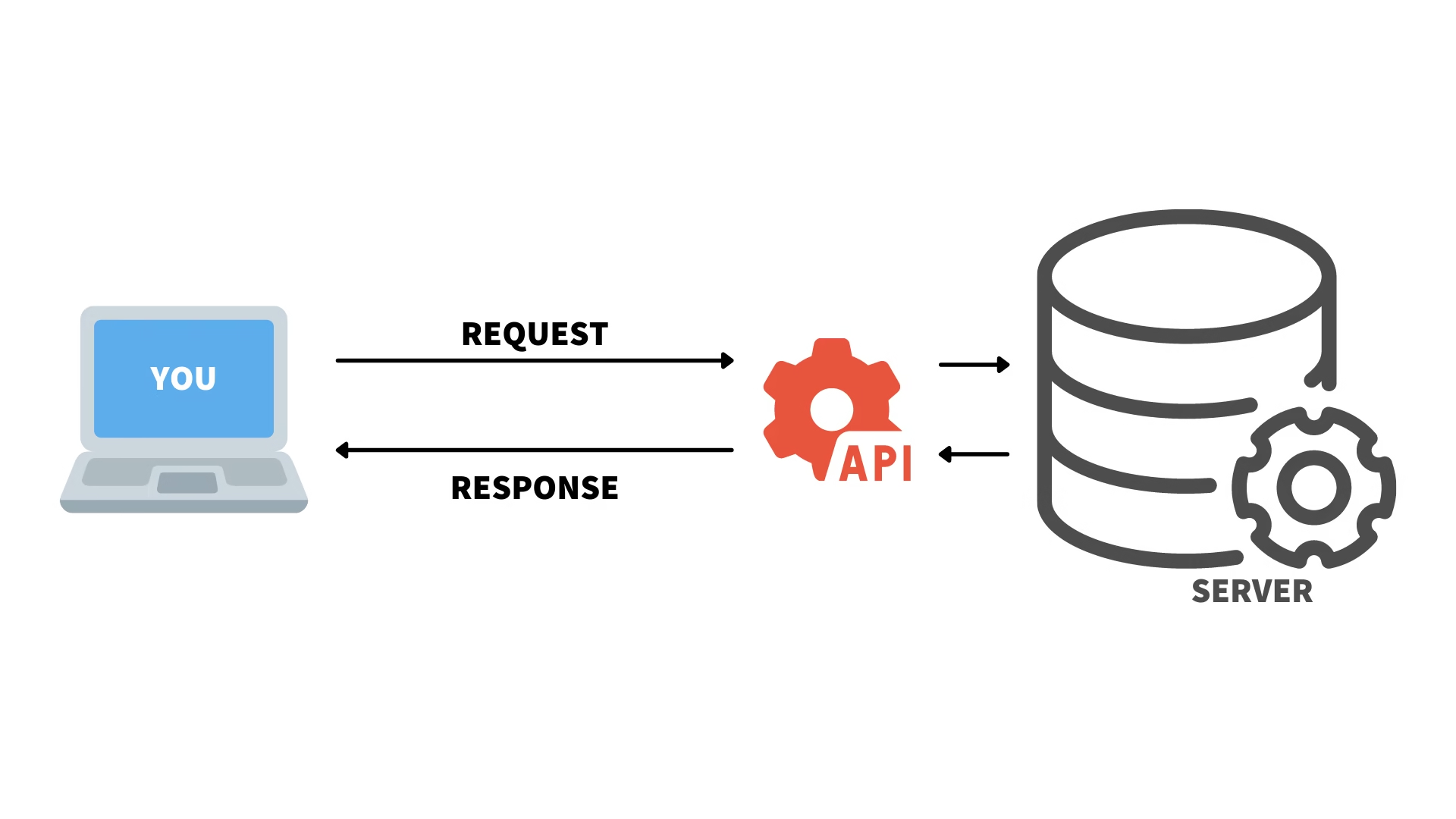
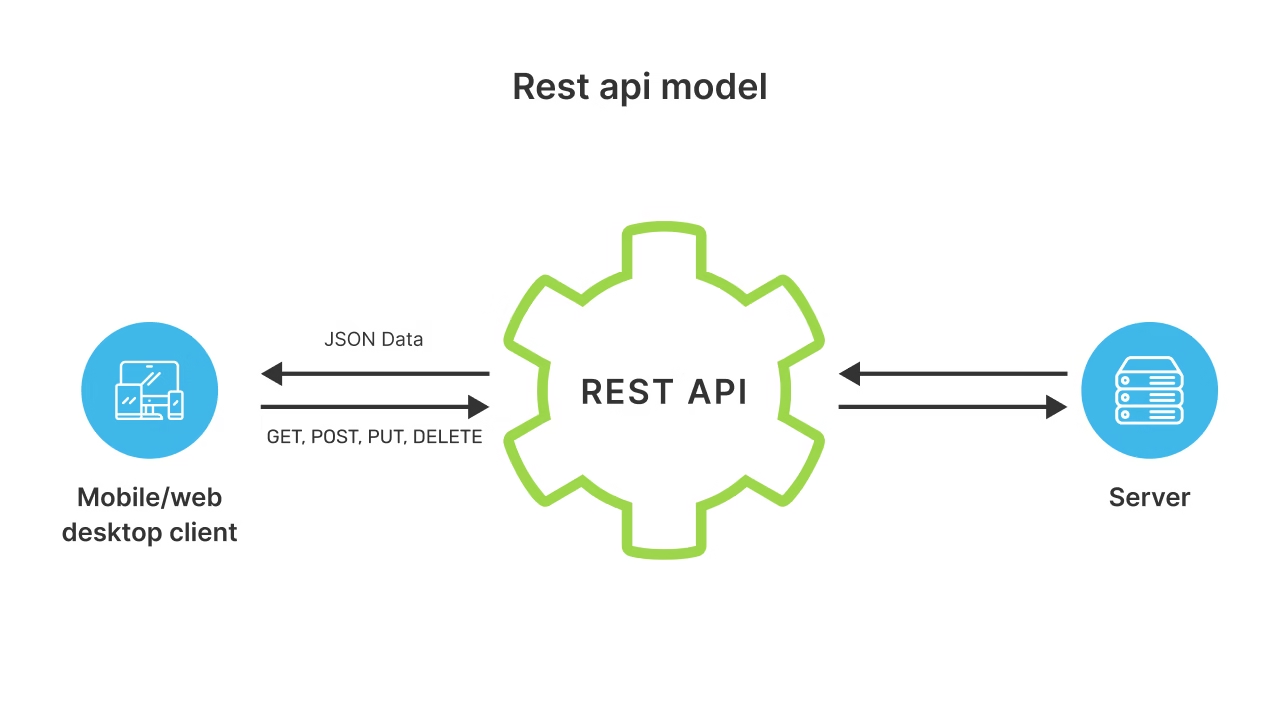
APIs are the backbone of modern web and mobile applications. But with great power comes great responsibility — especially when it comes to securing your APIs. That’s where authentication comes in. What is API Authentication? API authentication is the process of verifying the identity of the client or user who is trying to access an … Read more